“Citrix Receiver – Security Warning” explained and demystified
Author : Ingmar Verheij
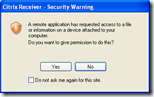 When you’ve worked with a Citrix XenApp or XenDesktop environment you must be familiar with the Security Warning dialog. It prevents a remote machine (your hosted application or desktop) from accessing resources on the client device, a security boundary you want to protect when from unmanaged systems.
When you’ve worked with a Citrix XenApp or XenDesktop environment you must be familiar with the Security Warning dialog. It prevents a remote machine (your hosted application or desktop) from accessing resources on the client device, a security boundary you want to protect when from unmanaged systems.
But on managed systems you want to prevent this message, you don’t want your users to be confronted with a message you tell them to accept (otherwise it won’t work and they’re to blame).
In this article I’ll explain why this message is displayed and how you can prevent it.
Resources types
A users can be confronted with a security warning dialog for different resources, this depends on the client used:
| Resource description | Client version < 12.0 | Client version > 12.0 |
| Client drives | X | X |
| Microphone and webcams | X | X (only audio) |
| PDA devices | X | – |
| USB and other devices | X | – |
Client versions
“Back in the old days”, or when you’re using Citrix Presentation Server 4.5 or older, a Citrix ICA Client is used with a version lower than 12.0. The security warning dialog can be configured with the webica.ini file in the users profile.
The Citrix Receiver (version 12.0 and up) ignores the webica.ini file and is solely configured via the registry. A new feature with the name ‘Client Selective Trust’ was introduced to allow a more fine grained configuration that can be set via a group policy.
Before version 12.0
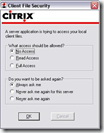
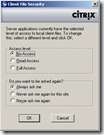
When you’re using a Citrix ICA client before version 12.0 the user will be asked what access level should be allowed. The users can choose between three access levels:
- No Access
- Read Access
- Full Access
Depending of the version used the following message will be displayed
Preventing the message
This message can be prevented by placing a webica.ini file in the %SystemRoot% (version 10.0 or lower) or the %AppData%\ICAClient directory (version 10.1 or higher).
The file has the following content
[Access] GlobalSecurityAccess=403 [AudioInput] GlobalSecurityAccess=803
Where the number represents an access level
| Access | AudioInput | ||
| -1 | No security setting configured | 803 | No Access, never ask me again |
| 403 | No Access | 804 | Full Access, never ask me again |
| 403 | Read Access | 806 | Never prompt current application |
| 405 | Full Access | 807 | Never prompt any application |
| 808 |
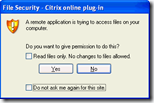
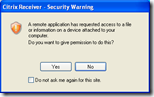
Version 12.0 and up (Citrix Receiver)
From Citrix Online Plugin 12.0 and up, including the current Citrix Receiver 3.x, users are presented the following dialog:
The content of the message depends on the resource that is accessed from the remote server.
GUID
For each target environment that is accessed a unique registry key is made in registry with the name HKCU\SOFTWARE\Citrix\ICA Client\Client Selective Trust\{GUID}. It seems that the {GUID} is generated during runtime and (therefore) cannot be predicted. You can find what GUID belongs to what connection by reading the value HKCU\SOFTWARE\Citrix\ICA Client\Client Selective Trust\{GUID}\RegionName\@.This value contains the name of the environment.
 If you connect via a webinterface / cloudgateway this key contains the URL (like lab.pepperbyte.com). When you connected directly to a published application / server via an ICA file the content will be something like ica://172.31.50.132:1494.
If you connect via a webinterface / cloudgateway this key contains the URL (like lab.pepperbyte.com). When you connected directly to a published application / server via an ICA file the content will be something like ica://172.31.50.132:1494.
Preventing the message
 The message van be configured per resource type, where each resource type is a subkey of ICA Client\Client Selective Trust\{GUID}IcaAuthorizationDecision (no \ after the GUID!).
The message van be configured per resource type, where each resource type is a subkey of ICA Client\Client Selective Trust\{GUID}IcaAuthorizationDecision (no \ after the GUID!).
| Resource type | Subkey |
| Client drives | FileSecurityPermission |
| Microphones and webcams | MicrophoneAndWebcamSecurityPermission |
| PDA devices | PdaSecurityPermission |
| USB and other devices | ScannerAndDigitalCameraSecurityPermission |
The access level can be set in the default (@) value where the number represents an access level
| Value | Description |
| 0 | No access |
| 1 | Read access |
| 2 | Full access |
| 3 | Prompt the user for access |
The access level can be set per accessed environment (per GUID) or per region. By configuring the access level on the HKEY_LOCAL_MACHINE (HKLM) hive instead on the HKEY_CURRENT_USER (HKCU) hive the setting is inherited by all users.
 If you can to configure the access permission per region you need to change the value of IsIsmDeferalEnabled to true and set the access level per resource type.
If you can to configure the access permission per region you need to change the value of IsIsmDeferalEnabled to true and set the access level per resource type.
The regions that can be configured in HKLM match the regions that can be found (and configured) in Internet Explorer.
| Zone | Subkey |
| Internet | oidInternetRegion |
| Local Intranet | oidIntranetRegion |
| Trusted sites | oidTrustedSitesRegion |
| Restricted sites | oidRestrictedSitesRegion |
Keep in mind that if you configure the settings on a x64 operating system the keys are stored in HKLM\SOFTWARE\Wow6432Node\Citrix\ICA Client\Client Selective Trust.
Was once an enthusiastic PepperByte employee but is now working at Citrix. His blogs are still valuable to us and we hope to you too.

Nice post. I was checking constantly this blog and I’m impressed!
Very useful information particularly the last part 🙂 I care for such information much.
I was looking for this particular information for a long
time. Thank you and best of luck.