Read DHCP options received by the client
When a DHCP client receives information from a DHCP server only basic information, like IP / subnet / gateway / dns /etc, is visible. In some situations clients also receive DHCP options to set specific settings or application configurations (for example with Microsoft Lync or RES Workspace Manager). Knowing what options are received by the clients helps you troubleshoot.
There are multiple road that lead to Rome, in this article I’ll show you three. For one of them I created a PowerShell script which you can run on any machine.
Three roads to Rome
Although there are probably more, here are three roads that lead to Rome (and with Rome I mean: reading the DHCP options received by the client).
- Wireshark
- DHCP test client
- Windows registry
Wireshark
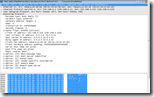 Wireshark gives you (by far) the most detailed information about the DHCP process and information received. Not only does it show you what information is received, it also shows you what packets are send / received over the network.
Wireshark gives you (by far) the most detailed information about the DHCP process and information received. Not only does it show you what information is received, it also shows you what packets are send / received over the network.
![]() All you have to do is install Wireshark on your computer (or run the portable version), start a capture, set the filter to bootp and initiate a DHCP request.
All you have to do is install Wireshark on your computer (or run the portable version), start a capture, set the filter to bootp and initiate a DHCP request.
DHCP test client
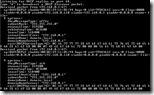 Another great tool to use is the DHCP test client. This sniffs the network until a DHCP Offer / DHCP Ack is detected on UDP port 68 and shows the received information.
Another great tool to use is the DHCP test client. This sniffs the network until a DHCP Offer / DHCP Ack is detected on UDP port 68 and shows the received information.
The benefit of the DHCP test client is that you don’t have to install anything, just run the tool and initiate a DHCP request.
Windows registry
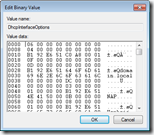 The downside of both Wireshark and the DHCP test tool is that you need to capture the packets from the network when they’re send. Luckily the received packets are stored in the Windows registry key DhcpInterfaceOptions.
The downside of both Wireshark and the DHCP test tool is that you need to capture the packets from the network when they’re send. Luckily the received packets are stored in the Windows registry key DhcpInterfaceOptions.
Unfortunately the content of this key is not easy to read and not documented (?). So without a tool / script the content of this key is useless.
PowerShell script
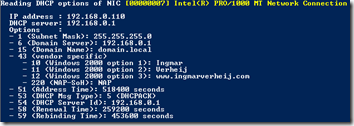
Since the DhcpInterfaceOptions is always accessible (even when the client already received the DHCP offer) I wanted to have the ability to read the content. So I wrote a PowerShell script that reads the registry key for each DHCP enabled NIC and shows the received DHCP options.
The script shows all Dhcp options and vendor specific Dhcp options (43).
You can find the PowerShell script here: ReadDhcpOptions
The archive contains three files
- DhcpOptions.csv – Semicolon separated file containing all Dhcp Options (IANA) and their data type;
- DhcpOptionsVS.csv – Semicolon separated file containing some vendor specific Dhcp Options;
- ReadDhcpOptions.ps1 – The actual PowerShell script
PS: My PowerShell-force is not strong, yet I managed to show the required data
Reverse engineering
Since the content of the DhcpInterfaceOptions key is not documented (or maybe I’ve searched on the wrong location) I had to reverse engineer the content. Once you know how the data is stored it’s really easy 🙂
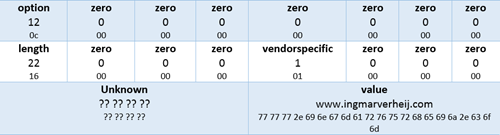
Each DHCP option the following structure is used:
- The first byte contains the option code, followed by 7 zeroed bytes;
- Next is a byte containing the length of the value, followed by 3 zeroed bytes;
- Then a byte specifying if this is a vendor specific option yes (1) or no (0), followed by 3 zeroed bytes;
- Four bytes are filled with data I can’t explain, but it always ends with 0x51.
- Finally the value is stored (in Hex values) in a block size dividable by 4 (!)
Here’s an example of how a vendor specific option (DHCP option 43) with code 12 containing the data www.ingmarverheij.com is stored:
Data types
To present the data, as done with the PowerShell script, you must know the data type. Unfortunately this is not stored in the DhcpInterfaceOptions key, so that’s the reason I added the CSV files. For now I included the following data type: ip / string / time / dhcpmsgtype.
If the data type is not specified in the CSV file the data is displayed in Hex values (just like Wireshark, DHCP test client and the Windows registry).
If you receive a Dhcp option that’s displayed in Hex values you can change the CSV files or e-mail me a Wireshark capture of your DHCPOFFER.
.
Was once an enthusiastic PepperByte employee but is now working at Citrix. His blogs are still valuable to us and we hope to you too.